
Enlarge / Please don't do this. (credit: Getty Images)
Passkeys are here to (try to) kill the password. Following Google's beta rollout of the feature in October, passkeys are now hitting Chrome stable M108. "Passkey" is built on industry standards and backed by all the big platform vendors—Google, Apple, Microsoft—along with the FIDO Alliance. Google's latest blog says: "With the latest version of Chrome, we're enabling passkeys on Windows 11, macOS, and Android." The Google Password Manager on Android is ready to sync all your passkeys to the cloud, and if you can meet all the hardware requirements and find a supporting service, you can now sign-in to something with a passkey.
Passkeys are the next step in evolution of password managers. Today password managers are a bit of a hack—the password text box was originally meant for a human to manually type text into, and you were expected to remember your password. Then, password managers started automating that typing and memorization, making it convenient to use longer, more secure passwords. Today, the right way to deal with a password field is to have your password manager generate a string of random, unmemorable junk characters to stick in the password field. The passkey gets rid of that legacy text box interface and instead stores a secret, passes that secret to a website, and if it matches, you're logged in. Instead of passing a randomly generated string of text, passkeys use the "WebAuthn" standard to generate a public-private keypair, just like SSH.
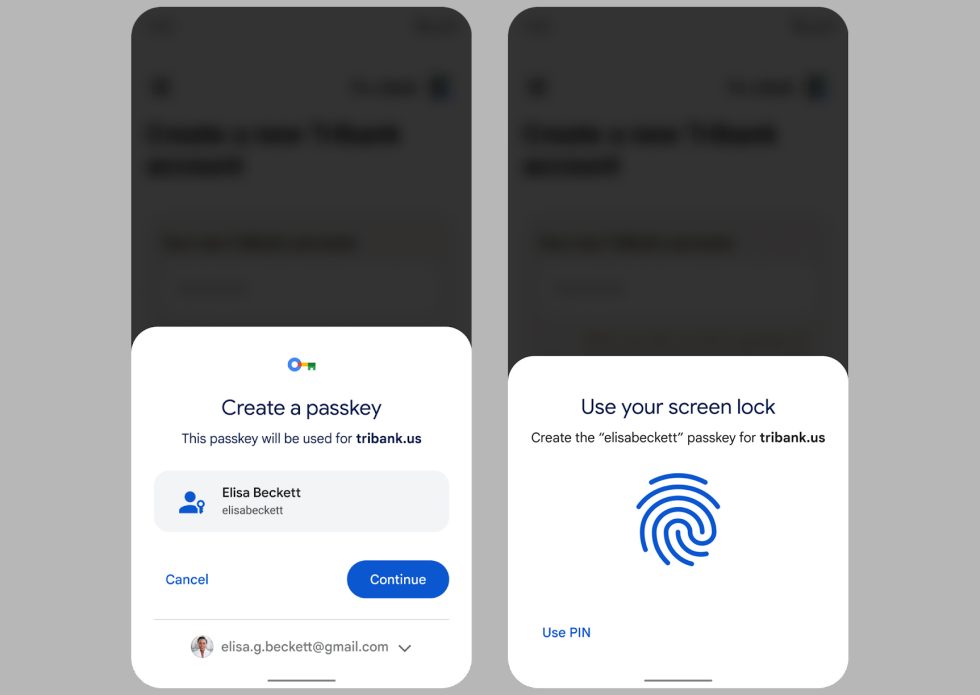
The passkey process works a lot like autofill. (credit: Ron Amadeo)
If everyone can figure out the compatibility issues, passkeys offer some big advantages over passwords. While passwords can be used insecurely with short text strings shared across many sites, a passkey is always enforced to be unique in content and secure in length. If a server breach happens, the hacker isn't getting your private key, and it's not a security issue the way a leaked password would be. Passkeys are not phishable, and because they require your phone to be physically present (!!) some random hacker from halfway around the world can't log in to your account anyway.
Read 6 remaining paragraphs | Comments

Enlarge / Please don't do this. (credit: Getty Images)
Passkeys are here to (try to) kill the password. Following Google's beta rollout of the feature in October, passkeys are now hitting Chrome stable M108. "Passkey" is built on industry standards and backed by all the big platform vendors—Google, Apple, Microsoft—along with the FIDO Alliance. Google's latest blog says: "With the latest version of Chrome, we're enabling passkeys on Windows 11, macOS, and Android." The Google Password Manager on Android is ready to sync all your passkeys to the cloud, and if you can meet all the hardware requirements and find a supporting service, you can now sign-in to something with a passkey.
Passkeys are the next step in evolution of password managers. Today password managers are a bit of a hack—the password text box was originally meant for a human to manually type text into, and you were expected to remember your password. Then, password managers started automating that typing and memorization, making it convenient to use longer, more secure passwords. Today, the right way to deal with a password field is to have your password manager generate a string of random, unmemorable junk characters to stick in the password field. The passkey gets rid of that legacy text box interface and instead stores a secret, passes that secret to a website, and if it matches, you're logged in. Instead of passing a randomly generated string of text, passkeys use the "WebAuthn" standard to generate a public-private keypair, just like SSH.

The passkey process works a lot like autofill. (credit: Ron Amadeo)
If everyone can figure out the compatibility issues, passkeys offer some big advantages over passwords. While passwords can be used insecurely with short text strings shared across many sites, a passkey is always enforced to be unique in content and secure in length. If a server breach happens, the hacker isn't getting your private key, and it's not a security issue the way a leaked password would be. Passkeys are not phishable, and because they require your phone to be physically present (!!) some random hacker from halfway around the world can't log in to your account anyway.
Read 6 remaining paragraphs | Comments
December 10, 2022 at 01:25AM

Post a Comment